Security Datascience
Some of things I made for the blue team to go offensive with AI
Mitigating Active Directory Attacks using AI
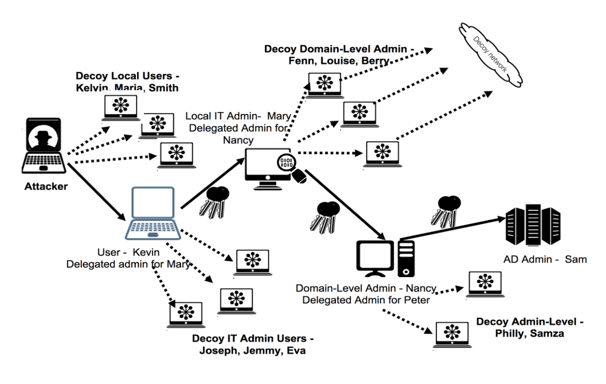
From a data science perspective, Active Directory security can be modeled as a graph problem, where nodes represent various entities (users, computers, groups) and edges represent relationships and permissions between them. Attackers typically leverage tools like BloodHound to analyze this graph structure and identify optimal attack paths with the least resistance to reach high-value targets like Domain Controllers, making attack path analysis a critical component of AD security assessment. Modern AD security challenges stem from the complexity of managing thousands of objects and their relationships, with factors like misconfigured permissions, legacy protocols, and patch management gaps creating a dynamically expanding attack surface that requires continuous monitoring and analysis. Detecting attack techniques like Kerberoasting is particularly challenging from a data science standpoint because the malicious activities blend in with normal business operations, making traditional anomaly detection approaches prone to false positives. Advanced security analytics and deception technology can help by creating and monitoring decoy targets within the AD structure, generating high-fidelity alerts when attackers interact with these honeypots, and enabling security teams to map and analyze potential attack paths proactively.


Deep-learning & Information security
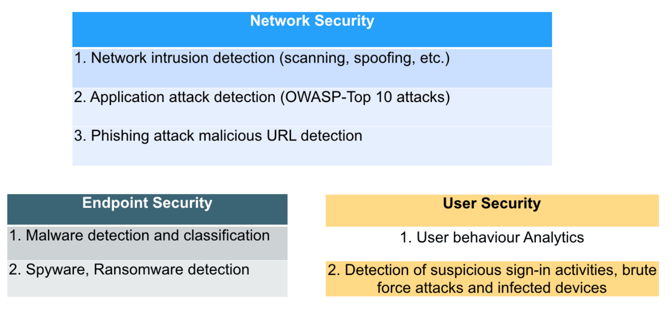
CDeep learning has emerged as a powerful tool in information security, particularly where substantial labeled datasets exist, though its application faces constraints due to limited availability of labeled security data. The technology has shown particular promise in network security applications, where Feed Forward Networks detect anonymous/TOR traffic, while Convolutional and Recurrent Neural Networks with LSTM architectures identify Command & Control domains. In ransomware detection, machine learning classifiers analyze DNS logs and domain characteristics using specialized features like bigram/trigram scores and Shannon entropy, achieving nearly 100% detection rates with low false positives when combined with deception technology. Rather than operating as a standalone solution, the most effective security implementations combine deep learning with other techniques like deception technology, shifting from broad-spectrum monitoring to more targeted, event-driven detection strategies. While deep learning isn't a universal solution for all information security challenges, it has demonstrated significant improvements over traditional rule-based systems, especially when integrated with modern security infrastructure like SIEMs and active system logging, marking a significant evolution in security data science approaches.
Modelling Attack using Game Theory
This research introduces a novel game-theoretic approach to cybersecurity defense, specifically focusing on protecting enterprise Active Directory systems through strategic deception. By modeling the network as an Abstract Network Graph (ANG) and implementing game theory principles, the study demonstrates how strategically placed fake users and credentials can effectively mislead attackers and increase their operational costs. The model incorporates sophisticated elements including exponential learning curves for attackers, cost-shading algorithms to mask high-value assets, and risk-based decision making, all validated through extensive simulations. Key findings reveal that deception significantly increases attacker workload, with network size and connectivity playing crucial roles in defense effectiveness. The research provides a mathematical framework for optimizing deception placement in enterprise networks, showing that combining deception with existing security measures improves overall defense capabilities, particularly against privilege escalation attacks. This work represents a significant advancement in quantitative approaches to deception-based cybersecurity, offering practical insights for enterprise network defense strategies.